This article was written on April 7, 2025. In an effort to maintain responsible disclosure, we have informed UP ITDC about this leak on April 7, 2025 to give them time to adjust permissions and to enact appropriate privacy and security protocols.
If you log in to your UP mail account right now and open up groups.google.com, you should only see one, two, or maybe a few lists you happen to be on. On the left-hand side though, you’ll see a little building icon on a section that says “All groups”. When you click this, you should see a handful of email lists. A bit odd. You scroll through and you realize, “oh, that feels like information I shouldn’t have.”
But even worse is when you click through into one of these Google Groups and realize you can read every single email in their threads. This is the predicament SINAG found itself in last week when we discovered this from a rarely-used Google feature– Google Groups.
Splashing about
Google Groups is a service run by Google to facilitate threaded discussions of common interests. If you are familiar with usenet and other discussion email threads and mailing lists from a long time ago, it is similar to that, but brought into the modern age.
For those who are unfamiliar though, a “mailing list” is essentially an email address that forwards any email it receives to the people “signed up” to the list. For example, the UP System email blast system allows OVCSA to forward information and events to UPD students without having to list out each student individually.
The intended purpose of Google Groups is, of course, simply to act like a decentralized forum based on a common mailing list address. However, as we have come to find out, these Google Groups are being treated like mailing lists, with reply-alls turning these threads into public-meant-private correspondence. As a result, these meant-to-be-fora have become a leaking ground for private information of students, faculty, and staff alike.
Here comes the flood
Worst hit among these is UP Manila, which has extensive Google Group mailing networks for a number of departments and colleges. While many of these emails are simply announcements befitting Google Groups and perhaps better served by a regular mailing list, a little bit of searching yields PDFs and spreadsheets with private information of thousands of students, faculty, and staff since at least2017.
While we would like to study the extent of this leak, its size has also necessitated proper and responsible disclosure to ensure the security of people’s private information. As a result, upon realizing how much information we were able to find, we compiled evidence of data leakage and sent a report to UP ITDC, alongside UPD’s Data Protection Office. CC’d in the email are the IT offices of UP Los Banos (UPLB Digital Innovation Center), UP Baguio (UPB LAN Office), UP Manila (UPM Information Management Service), and UP-PGH (UP PGH Information Technology Office).
Here are some of the things we found as we looked through some of the emails:
- at least 13,108 email addresses linked to Canva accounts (several hundreds of which are also linked to personal email accounts)
- at least 1,300 UP Manila employee numbers and email addresses
- at least 500 UP student numbers
- at least 100 UP student home/current addresses
- at least 30 UP student Weighted Average Grades with graduation eligibility statuses
- … and possibly more that we have not yet had the time to comb through.
Spore growth, water damage
Earlier this week, an email was sent to the up_users-list, which was sent to student across the UP System by someone using the AnonymousEmail service. It was simply titled “Basic user testing” and contained only three words: “Get krunked idiots”.
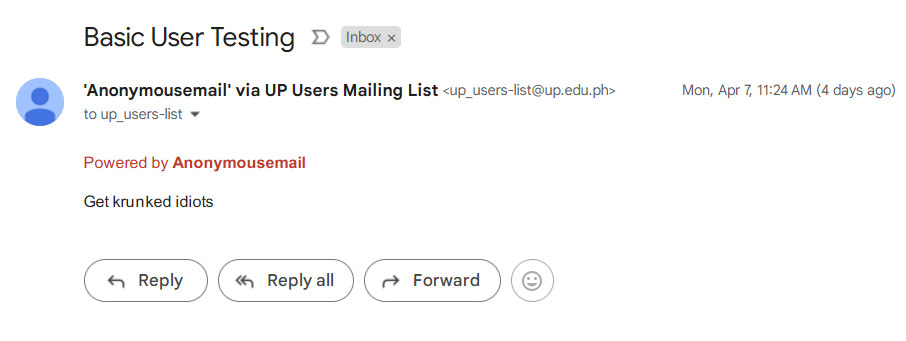
This spurred concerns about the integrity of UP’s IT infrastructure, especially coming off the heels of Tinig ng Plaridel’s article on how improper access controls for student files led to many meant-to-be-private files to become accessible to everyone in the UP System Google Workspace. The Google Groups leak is similarly a problem of access control and is similarly a long-term problem that has been left unchecked.
Security breaches sometimes come about due to hacks or malicious actors. However, more often, security breaches and data privacy violations are often the result of improper access controls and permissions. When we upload things to the internet or send them to other people, it is important to have a good grasp of who is allowed to read and save that information.
In the case of Google Drive files, it does tell you that by setting it to “Anyone in the University of the Philippines”, it can be seen by… well, anyone in the University of the Philippines. However, users continue to make use of the option. Why?
Part of the issue is perhaps ambivalence. Many of these files do not really have lasting importance to students and are simply documents they need to have for class or are documents they want to share and can not really be bothered to be inconvenienced to get individual people’s emails to properly set security. After all, most of the time security often costs convenience and why would one want to be inconvenienced for security for a file I won’t care about in a week?
Another part of the issue is perhaps lack of knowledge. Many students are taught very simplistically about access and permissions and might unquestioningly follow the practices of others, even if it is not secure. Data privacy breaches have become commonplace and it is becoming increasingly clear that, despite UP ITDC’s continued warnings and memoranda, many UP students do not really understand the gravity of their digital footprint inside the UP system.
Black mold
In previous years, CSSP has been hit by a variety of impersonation scandals. Students who have claimed to be parts of the Political Science department, among others, have led to heightened awareness inside the College based on information provided by the UP POLIS Core Group’s Student Rights and Welfare (STRAW) Committee. However, if the college was more impacted by the Google Groups leak, someone could have stolen the identity of someone inside UP and used it to infiltrate student organizations.
It is already well-known inside UP how often state actors and malicious elements have intruded on student spaces. And with these data breaches and threats, there is a worry that the leaking water damage has allowed a mold to take hold.
And when a black mold has infested someone’s home, there is an unruly paranoia that takes over. Who can you trust when your infrastructure has time and again failed to protect you? How will we talk online when mistrust is being sowed faster than we can grow our communities?
As we hurtle towards a world full of deepfaked voices, AI-generated imagery, and fake news on the horizon, our closest circles need to have secure systems we rely on. We need to be able to understand and embrace the provenance of data and information in the world. Because when we can no longer verify, there’s nothing left to fall back on but trust.
The cleaners
The responsibility of maintaining these systems is paramount, as they undergird many of our systems in day-to-day study and life. When major privacy leaks happen in UP, I end up reflecting on how our systems nationally hold up. I wonder about all that voter data and healthcare information floating around being traded in the unkempt corners of the internet.
Then I remembered how malicious actors are everywhere. The Philippines itself has become a testing ground for social media destabilization. But even bigger networks for free information such as LibGen and Z-Library continue to be under threat, both legally and stability-wise.
There are many very smart people working on our systems, both for us to trust and for us to verify. Some of them work on ours. In UP Diliman, we have the UP Computer Center, for example. So we reached out to them about this leak.
As of this article’s publication, we have had correspondence with UP Baguio LAN Office for clarifications.
UP ITDC has also provided the following comment with regards to the disclosure report:
We appreciate your feedback regarding the use of Groups in our Google Suite for Education.
In response to this, we have again reminded our UP users about the policy of Google regarding the use of their services, one of these services is the Google Groups.
Similar to the use of Google Drive, the permissions on sharing contents/files must be properly tagged by our users. To orient and inform our users about the proper use of the Google applications, in addition to our regular IT advisories, the following activities/campaigns have been conducted:
Year 2024
- Webinar on How to Utilize Google and Microsoft 365’s Online Storage (April 5, 2024)
- Webinar on Google Workspace for Education Office Productivity and Collaboration Tools (March 8, 2024)
Year 2023
- Google Workspace End User Training by OVPAA (December 14, 2023)�
- Webinar on Google Suite for Education for Work, Office Productivity, and Collaboration Tools (March 23, 2023)
Year 2022
- Webinar on Google Drive (November 10, 2022)�
- Webinar on What’s New with Google Workspace for Education? (November 3, 2022)�
Year 2021
- Webinar on Google Drive (September 3, 2021)�
- Webinar on Google Suite for Education for Work Office Productivity and Collaboration Tools (January 25, 2021)
Year 2020
- Webinar on Basic Information Security (November 16, 2020)
- Webinar on Privacy Tips and Awareness (April 14, 2020)
- Webinar on Basic Information Security (March 30, 2020)
- Webinar on Google Suite for Education (April 1 and 8, 2020)�
- Webinar on Google Apps for Work Office Productivity and Collaboration Tools (April 1, 2020)�
In today’s advisory (April 10), we reiterated the policy of Google regarding the use of their services, as follows:
Google’s Terms of Service: https://policies.google.com/terms?hl=en
Specific terms on sharing of contents: https://policies.google.com/terms?hl=en#toc-content
FAQ page on Google Groups: https://itdc.up.edu.ph/faqs/google-groups-settings
Again, we thank you for informing us about improper tagging of content sharing permissions. Together with your publication and the whole UP community, we will continue to reach out to our digital users and share with them valuable information on how to protect their data, particularly their personal information.
Please do not hesitate to contact us again if you have any additional information useful to our community members. Your inputs and feedback will highly be appreciated.
While we appreciate these efforts, it is notable that we can not be safe solely through other people’s protections. The mold has grown and it is only through a concerted collective effort for better data privacy and security that we can keep each other safe– to look out for one another. There is a flood coming and we have to fix the leaks before it does.






rent a car jordan aqaba https://drivelity.com/car-rental-aqaba-jordan